Lazy Admin
https://tryhackme.com/room/lazyadmin
Open Ports:
- 21: ssh
- 80: HTTP
Port 80:
- find sub-doamisn and directories using dirb
- ip/content (we find sweetrice)
- ip/content/as (login Page)
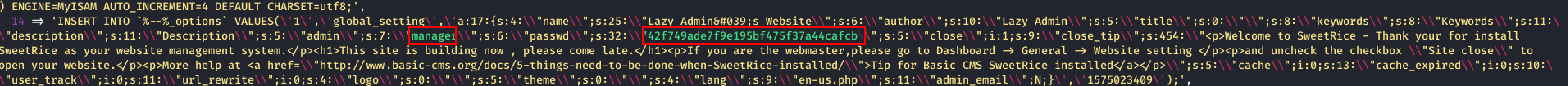
- ip/content/inc/mysqlbackup (found username and password)
Gaining Access:
SweetRice has a Remote Code Execution vulnerablitiy
- Uploading a php reverse shell in themes
- listening via netcat will gain you access to the BOX
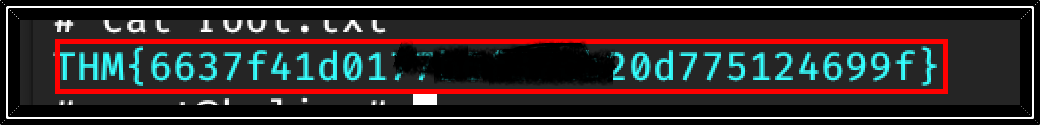
USER Flag:
Privilege Escalation:
- sudo -l
- This will show about things you can run as sudo
- On tracing the flie Paths we find we can edit /etc/copy.sh
Edit the IP and the PORT
- Executing the file and listening to it via netcat will give to root access
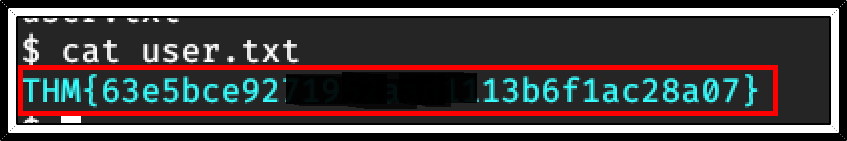
Root Flag: